[ad_1]
A cyberattack that shut down two of the highest casinos in Las Vegas final 12 months shortly grew to become some of the riveting safety tales of 2023. It was the primary recognized case of native English-speaking hackers in the USA and Britain teaming up with ransomware gangs primarily based in Russia. However that made-for-Hollywood narrative has eclipsed a much more hideous development: Many of those younger, Western cybercriminals are additionally members of fast-growing on-line teams that exist solely to bully, stalk, harass and extort weak teenagers into bodily harming themselves and others.

Picture: Shutterstock.
In September 2023, a Russian ransomware group often known as ALPHV/Black Cat claimed credit score for an intrusion on the MGM Resorts lodge chain that shortly introduced MGM’s casinos in Las Vegas to a standstill. Whereas MGM was nonetheless attempting to evict the intruders from its programs, a person who claimed to have firsthand data of the hack contacted a number of media shops to supply interviews about the way it all went down.
One account of the hack got here from a 17-year-old in the UK, who informed reporters the intrusion started when one of many English-speaking hackers phoned a tech assist particular person at MGM and tricked them into resetting the password for an worker account.
The safety agency CrowdStrike dubbed the group “Scattered Spider,” a recognition that the MGM hackers got here from completely different cliques scattered throughout an ocean of Telegram and Discord servers devoted to financially-oriented cybercrime.
Collectively, this archipelago of crime-focused chat communities is named “The Com,” and it features as a sort of distributed cybercriminal social community that facilitates prompt collaboration.
However principally, The Com is a spot the place cybercriminals go to boast about their exploits and standing inside the neighborhood, or to knock others down a peg or two. High Com members are consistently sniping over who pulled off probably the most spectacular heists, or who has collected the largest pile of stolen digital currencies.
And as typically as they extort sufferer firms for monetary acquire, members of The Com try to wrest stolen cash from their cybercriminal rivals — typically in ways in which spill over into bodily violence in the actual world.
CrowdStrike would go on to supply and promote Scattered Spider motion figures, and it featured a life-sized Scattered Spider sculpture at this 12 months’s RSA Safety Convention in San Francisco.
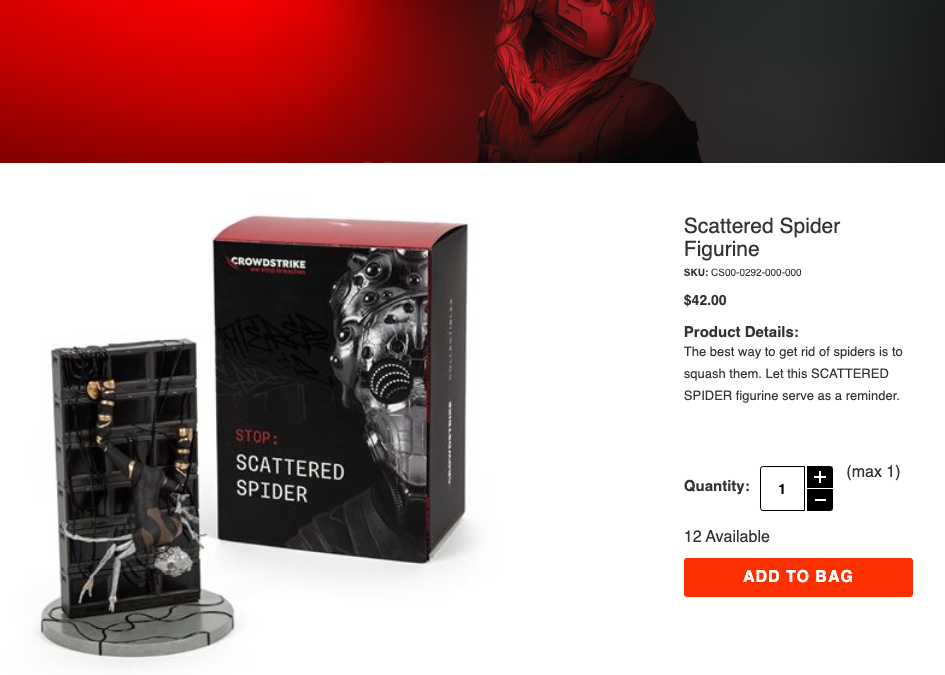
However advertising and marketing safety services and products primarily based on particular cybercriminal teams will be difficult, notably if it seems that robbing and extorting victims is under no circumstances probably the most abhorrent exercise these teams interact in every day.
KrebsOnSecurity examined the Telegram person ID variety of the account that provided media interviews in regards to the MGM hack — which corresponds to the display identify “@Holy” — and located the identical account was used throughout a lot of cybercrime channels which are completely targeted on extorting younger folks into harming themselves or others, and recording the hurt on video.
HOLY NAZI
Holy was recognized to own a number of prized Telegram usernames, together with @bomb, @halo, and @cute, in addition to one of many highest-priced Telegram usernames ever put up on the market: @nazi.
In a single put up on a Telegram channel devoted to youth extortion, this similar person will be seen asking if anybody is aware of the present Telegram handles for a number of core members of 764, an extremist group recognized for victimizing youngsters by coordinated on-line campaigns of extortion, doxing, swatting and harassment.
Individuals affiliated with hurt teams like 764 will typically recruit new members by lurking on gaming platforms, social media websites and cell purposes which are standard with younger folks, together with Discord, Minecraft, Roblox, Steam, Telegram, and Twitch.
“The sort of offence often begins with a direct message by gaming platforms and might transfer to extra non-public chatrooms on different digital platforms, usually one with video enabled options, the place the dialog shortly turns into sexualized or violent,” warns a current alert from the Royal Canadian Mounted Police (RCMP) in regards to the rise of sextortion teams on social media channels.
“One of many ways being utilized by these actors is sextortion, nevertheless, they aren’t utilizing it to extract cash or for sexual gratification,” the RCMP continued. “As an alternative they use it to additional manipulate and management victims to supply extra dangerous and violent content material as a part of their ideological aims and radicalization pathway.”
The 764 community is among the many most populated hurt communities, however there are a lot extra. Among the largest such recognized teams embody CVLT, Court docket, Kaskar, Leak Society, 7997, 8884, 2992, 6996, 555, Slit City, 545, 404, NMK, 303, and H3ll.
In March, a consortium of reporters from Wired, Der Spiegel, Recorder and The Washington Submit examined tens of millions of messages throughout greater than 50 Discord and Telegram discussion groups.
“The abuse perpetrated by members of com teams is excessive,” Wired’s Ali Winston wrote. “They’ve coerced youngsters into sexual abuse or self-harm, inflicting them to deeply lacerate their our bodies to carve ‘cutsigns’ of an abuser’s on-line alias into their pores and skin.” The story continues:
“Victims have flushed their heads in bathrooms, attacked their siblings, killed their pets, and in some excessive cases, tried or died by suicide. Court docket information from the USA and European nations reveal contributors on this community have additionally been accused of robberies, in-person sexual abuse of minors, kidnapping, weapons violations, swatting, and homicide.”
“Some members of the community extort youngsters for sexual pleasure, some for energy and management. Some do it merely for the kick that comes from manipulation. Others promote the express CSAM content material produced by extortion on the darkish internet.”
KrebsOnSecurity has discovered Holy is the 17-year-old who was arrested in July 2024 by the U.Okay.’s West Midlands Police as a part of a joint investigation with the FBI into the MGM hack.
Early of their cybercriminal profession (as a 15-year-old), @Holy glided by the deal with “Vsphere,” and was a proud member of the LAPSUS$ cybercrime group. All through 2022, LAPSUS$ would hack and social engineer their means into among the world’s greatest know-how firms, together with EA Video games, Microsoft, NVIDIA, Okta, Samsung, and T-Cell.
JUDISCHE/WAIFU
One other well timed instance of the overlap between hurt communities and prime members of The Com will be present in a bunch of criminals who not too long ago stole obscene quantities of buyer information from customers of the cloud information supplier Snowflake.
On the finish of 2023, malicious hackers discovered that many main firms have uploaded huge quantities of useful and delicate buyer information to Snowflake servers, all of the whereas defending these Snowflake accounts with little greater than a username and password (no multi-factor authentication required). The group then searched darknet markets for stolen Snowflake account credentials, and started raiding the information storage repositories utilized by among the world’s largest firms.
Amongst people who had information uncovered in Snowflake was AT&T, which disclosed in July that cybercriminals had stolen private info and telephone and textual content message information for roughly 110 million folks — almost all its clients.
A report on the extortion group from the incident response agency Mandiant notes that Snowflake sufferer firms had been privately approached by the hackers, who demanded a ransom in trade for a promise to not promote or leak the stolen information. All informed, greater than 160 organizations had been extorted, together with TicketMaster, Lending Tree, Advance Auto Elements and Neiman Marcus.
On Could 2, 2024, a person by the identify “Judische” claimed on the fraud-focused Telegram channel Star Chat that that they had hacked Santander Financial institution, one of many first recognized Snowflake victims. Judische would repeat that declare in Star Chat on Could 13 — the day earlier than Santander publicly disclosed an information breach — and would periodically blurt out the names of different Snowflake victims earlier than their information even went up on the market on the cybercrime boards.
A cautious evaluate of Judische’s account historical past and postings on Telegram exhibits this person is extra broadly recognized underneath the nickname “Waifu,” an early moniker that corresponds to one of many extra completed SIM-swappers in The Com over time.
In a SIM-swapping assault, the fraudsters will phish or buy credentials for cell phone firm staff, and use these credentials to redirect a goal’s cell calls and textual content messages to a tool the attackers management.
A number of channels on Telegram keep a steadily up to date leaderboard of the 100 richest SIM-swappers, in addition to the hacker handles related to particular cybercrime teams (Waifu is ranked #24). That leaderboard has lengthy included Waifu on a roster of hackers for a bunch that known as itself “Beige.”
Beige members had been implicated in two tales revealed right here in 2020. The primary was an August 2020 piece known as Voice Phishers Concentrating on Company VPNs, which warned that the COVID-19 epidemic had introduced a wave of voice phishing or “vishing” assaults that focused work-from-home staff through their cell gadgets, and tricked a lot of these folks into giving up credentials wanted to entry their employer’s community remotely.
Beige group members even have claimed credit score for a breach on the area registrar GoDaddy. In November 2020, intruders considered related to the Beige Group tricked a GoDaddy worker into putting in malicious software program, and with that entry they had been in a position to redirect the online and electronic mail visitors for a number of cryptocurrency buying and selling platforms.
The Telegram channels that Judische and his associated accounts frequented over time present this person divides their time between posting in SIM-swapping and cybercrime cashout channels, and harassing and stalking others in hurt communities like Leak Society and Court docket.
Mandiant has attributed the Snowflake compromises to a bunch it calls “UNC5537,” with members primarily based in North America and Turkey. KrebsOnSecurity has discovered Judische is a 26-year-old software program engineer in Ontario, Canada.
Sources near the investigation into the Snowflake incident inform KrebsOnSecurity the UNC5537 member in Turkey is John Erin Binns, an elusive American man indicted by the U.S. Division of Justice (DOJ) for a 2021 breach at T-Cell that uncovered the private info of no less than 76.6 million clients.
Binns is at the moment in custody in a Turkish jail and preventing his extradition. In the meantime, he has been suing nearly each federal company and agent that contributed investigative sources to his case.
In June 2024, a Mandiant worker informed Bloomberg that UNC5537 members have made demise threats in opposition to cybersecurity specialists investigating the hackers, and that in a single case the group used synthetic intelligence to create faux nude photographs of a researcher to harass them.
ViLE
In June 2024, two American males pleaded responsible to hacking right into a U.S. Drug Enforcement Company (DEA) on-line portal that tapped into 16 completely different federal legislation enforcement databases. Sagar “Weep” Singh, a 20-year-old from Rhode Island, and Nicholas “Convict” Ceraolo, 25, of Queens, NY, had been each lively in SIM-swapping communities.
Singh and Ceraolo hacked into a lot of international police division electronic mail accounts, and used them to make phony “emergency information requests” to social media platforms looking for account details about particular customers they had been stalking. In response to the federal government, in every case the lads impersonating the international police departments informed these platforms the request was pressing as a result of the account holders had been buying and selling in little one pornography or participating in little one extortion.
Finally, the 2 males fashioned a part of a bunch of cybercriminals recognized to its members as “ViLE,” who concentrate on acquiring private details about third-party victims, which they then used to harass, threaten or extort the victims, a apply often known as “doxing.”
The U.S. authorities says Singh and Ceraolo labored intently with a 3rd man — referenced within the indictment as co-conspirator #1 or “CC-1” — to manage a doxing discussion board the place victims may pay to have their private info eliminated.
The federal government doesn’t identify CC-1 or the doxing discussion board, however CC-1’s hacker deal with is “Kayte” (a.ok.a. “KT“) which corresponds to the nickname of a 23-year-old man who lives together with his dad and mom in Coffs Harbor, Australia. For a number of years (with a short interruption), KT has been the administrator of a really vile doxing neighborhood often known as the Doxbin.

A screenshot of the web site for the cybercriminal group “ViLE.” Picture: USDOJ.
Individuals whose names and private info seem on the Doxbin can shortly discover themselves the goal of prolonged harassment campaigns, account hacking, SIM-swapping and even swatting — which entails falsely reporting a violent incident at a goal’s tackle to trick native police into responding with doubtlessly lethal pressure.
A handful of Com members focused by federal authorities have gone as far as to perpetrate swatting, doxing, and different harassment in opposition to the identical federal brokers who’re attempting to unravel their alleged crimes. This has led some investigators working instances involving the Com to start redacting their names from affidavits and indictments filed in federal court docket.
In January 2024, KrebsOnSecurity broke the information that prosecutors in Florida had charged a 19-year-old alleged Scattered Spider member named Noah Michael City with wire fraud and identification theft. That story recounted how City’s alleged hacker identities “King Bob” and “Sosa” inhabited a world wherein rival cryptocurrency theft rings steadily settled disputes by so-called “violence-as-a-service” choices — hiring strangers on-line to perpetrate firebombings, beatings and kidnappings in opposition to their rivals.
City’s indictment exhibits the identify of the federal agent who testified to it has been blacked out:
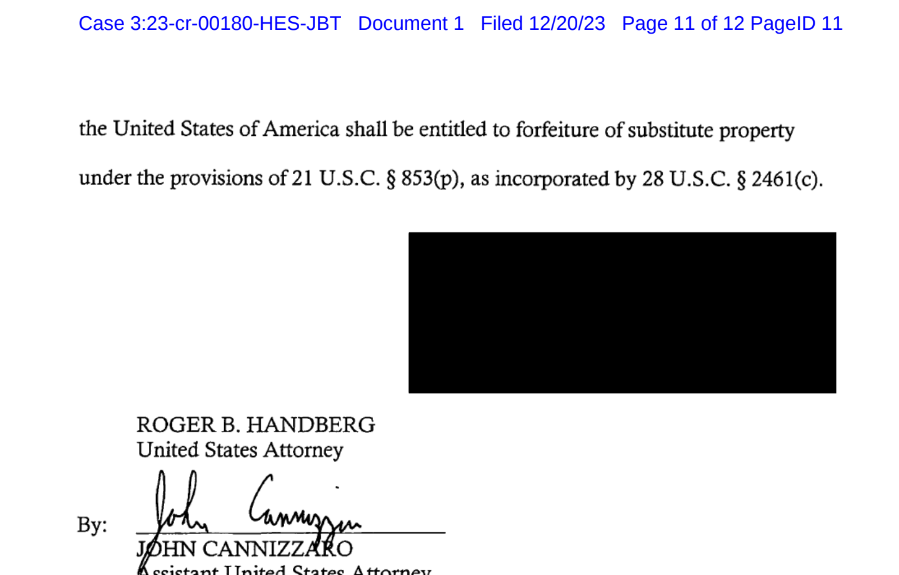
The ultimate web page of Noah Michael City’s indictment exhibits the investigating agent redacted their identify from charging paperwork.
HACKING RINGS, STALKING VICTIMS
In June 2022, this weblog informed the story of two males charged with hacking into the Ring residence safety cameras of a dozen random folks after which methodically swatting every of them. Including insult to harm, the lads used the compromised safety cameras to document reside footage of native police swarming these houses.

McCarty, in a mugshot.
James Thomas Andrew McCarty, Charlotte, N.C., and Kya “Chumlul” Nelson, of Racine, Wisc., conspired to hack into Yahoo electronic mail accounts belonging to victims in the USA. The 2 would test what number of of these Yahoo accounts had been related to Ring accounts, after which goal individuals who used the identical password for each accounts.
The Telegram and Discord aliases allegedly utilized by McCarty — “Aspertaine” and “Sofa,” amongst others — correspond to an identification that was lively in sure channels devoted to SIM-swapping.
What KrebsOnSecurity didn’t report on the time is that each ChumLul and Aspertaine had been lively members of CVLT, whereby these identities clearly participated in harassing and exploiting younger teenagers on-line.
In June 2024, McCarty was sentenced to seven years in jail after pleading responsible to creating hoax calls that elicited police SWAT responses. Nelson additionally pleaded responsible and obtained a seven-year jail sentence.
POMPOMPURIN
In March 2023, U.S. federal brokers in New York introduced they’d arrested “Pompompurin,” the alleged administrator of Breachforums, an English-language cybercrime discussion board the place hacked company databases steadily seem on the market. In instances the place the sufferer group isn’t extorted upfront by hackers, being listed on Breachforums has typically been the way in which many victims first discovered of an intrusion.
Pompompurin had been a nemesis to the FBI for a number of years. In November 2021, KrebsOnSecurity broke the information that 1000’s of pretend emails a couple of cybercrime investigation had been blasted out from the FBI’s electronic mail programs and Web addresses.
Pompompurin took credit score for that stunt, and stated he was in a position to ship the FBI electronic mail blast by exploiting a flaw in an FBI portal designed to share info with state and native legislation enforcement authorities. The FBI later acknowledged {that a} software program misconfiguration allowed somebody to ship the faux emails.
In December, 2022, KrebsOnSecurity detailed how hackers lively on BreachForums had infiltrated the FBI’s InfraGard program, a vetted community designed to construct cyber and bodily risk info sharing partnerships with specialists within the non-public sector. The hackers impersonated the CEO of a significant monetary firm, utilized for InfraGard membership within the CEO’s identify, and had been granted admission to the neighborhood.
The feds named Pompompurin as 21-year-old Peekskill resident Conor Brian Fitzpatrick, who was initially charged with one rely of conspiracy to solicit people to promote unauthorized entry gadgets (stolen usernames and passwords). However after FBI brokers raided and searched the house the place Fitzpatrick lived together with his dad and mom, prosecutors tacked on costs for possession of kid pornography.
DOMESTIC TERRORISM?
Current actions by the DOJ point out the federal government is effectively conscious of the numerous overlap between main members of The Com and hurt communities. However the authorities is also rising extra delicate to the criticism that it could typically take months or years to assemble sufficient proof to criminally cost a few of these suspects, throughout which period the perpetrators can abuse and recruit numerous new victims.
Late final 12 months, nevertheless, the DOJ signaled a brand new tactic in pursuing leaders of hurt communities like 764: Charging them with home terrorism.
In December 2023, the federal government charged (PDF) a Hawaiian man with possessing and sharing sexually specific movies and pictures of prepubescent youngsters being abused. Prosecutors allege Kalana Limkin, 18, of Hilo, Hawaii, admitted he was an affiliate of CVLT and 764, and that he was the founding father of a splinter hurt group known as Cultist. Limkin’s Telegram profile exhibits he additionally was lively on the hurt neighborhood Slit City.
The related quotation from Limkin’s criticism reads:
“Members of the group ‘764’ have conspired and proceed to conspire in each on-line and in-person venues to interact in violent actions in furtherance of a Racially Motivated Violent Extremist ideology, wholly or partially by actions that violate federal felony legislation assembly the statutory definition of Home Terrorism, outlined in Title 18, United States Code, § 2331.”
Consultants say charging hurt teams underneath anti-terrorism statutes doubtlessly provides the federal government entry to extra expedient investigative powers than it could usually have in a run-of-the-mill felony hacking case.
“What it in the end will get you is extra instruments you should use within the investigation, presumably warrants and issues like that,” stated Mark Rasch, a former U.S. federal cybercrime prosecutor and now basic counsel for the New York-based cybersecurity agency Unit 221B. “It might probably additionally get you extra cures on the finish of the case, like higher sanctions, extra jail time, fines and forfeiture.”
However Rasch stated this tactic can backfire on prosecutors who overplay their hand and go after somebody who finally ends up difficult the costs in court docket.
“For those who’re going to cost a hacker or pedophile with a criminal offense like terrorism, that’s going to make it tougher to get a conviction,” Rasch stated. “It provides to the prosecutorial burden and will increase the probability of getting an acquittal.”
Rasch stated it’s unclear the place it’s applicable to attract the road in the usage of terrorism statutes to disrupt hurt teams on-line, noting that there actually are circumstances the place people can commit violations of home anti-terrorism statutes by their Web exercise alone.
“The Web is a platform like every other, the place nearly any sort of crime that may be dedicated in the actual world can be dedicated on-line,” he stated. “That doesn’t imply all misuse of computer systems suits inside the statutory definition of terrorism.”
The RCMP’s advisory on sexual extortion of minors over the Web lists a lot of potential warning indicators that teenagers could exhibit in the event that they grow to be entangled in these hurt teams. The FBI urges anybody who believes their little one or somebody they know is being exploited to contact their native FBI discipline workplace, name 1-800-CALL-FBI, or report it on-line at ideas.fbi.gov.
[ad_2]
